Asset Management System
Introduction
Asset Management System is the Smart management of assets and tracking, which the system promotes, automatically translates to optimum utilization of resources; reduce cost of operation and care of the environment, national and global development, and scope of employment generation. And, it manages your IT assets from asset procuring to the asset retirement. These compliances the reduce your IT operational cost up to 40% by managing the asset. IT asset management (ITAM) is a business process that involves managing an organization's IT assets throughout their lifecycle:
- Identifying: Identifying what assets are needed and how to obtain them.
- Tracking: Tracking the status of IT assets using financial, contractual, and inventory data.
- Managing: Managing the acquisition, usage, maintenance, and retirement of IT assets.
- Optimizing: Optimizing the use of IT assets to minimize costs and maximize value.
ITAM is also known as IT asset lifecycle management or asset lifecycle management. It is different from IT operations management, which focuses on delivering IT services and system performance.
ITAM can help organizations to reduce costs by avoiding unnecessary purchases and reducing license and support fees. So, what is an IT asset? Defined simply, an IT asset includes hardware, software systems, or information an organization value.
IT asset management is not a project. You do not do it once and expect it to be finished. ITAM is a process that teams execute on a regular basis or as assets, goals, and tools change.
- Inventory assets: The first step in the IT asset management process is to create a detailed inventory of all IT assets. Your inventory includes what assets you have, where they are located when they were purchased, and for how much.
- Calculate lifecycle costs: The second step is to calculate lifecycle costs for all assets in your inventory. During an average asset’s life, there are many opportunities for added costs, like maintenance, capital, and disposal costs. Calculating lifecycle costs makes your asset inventory accurate and actionable.
- Tracking: The third step is tracking via an asset management tool. Your goal is to continuously monitor IT assets through their lifecycle keeping a close eye on things like contract, license, and warranty expiration. Tracking also helps you stay ahead of the fourth step, maintenance.
- Maintenance: Maintenance involves asset repair, upgrade, and replacement. All maintenance activities should be tracked in an ITAM tool so that the data can be used to understand the overall performance of the asset.
- Financial Planning: The fifth and final step is financial planning. With an accurate picture of your IT assets, their lifecycle stage, and their costs, you can effectively plan in future. One goal of financial planning is to determine the budget needed to maintain or improve the “levels of service” your team provides for your most important assets. An asset that was successfully managed with a high level of service, like a service desk and dedicated team, will need that level of service going forward. Assets that underperformed may need a higher level of service in the future, which will cost more
Features: -
1. Procurement
Procurement application enables users with an appropriate procurement role to manage purchase order information for assets. It also provides direct access to service catalogue requests. You can create purchase orders and transfer orders directly from requests. Before using the Procurement application, create assignment groups for catalogue tasks. Assignment groups are sets of users, filtered by location, who can perform catalogue tasks.
2. Asset Management
2.1 HAM: Hardware asset management (HAM) is the process of managing the physical components of computers, computer networks and systems. This begins with acquisition and continues through maintenance until the hardware's ultimate disposal. This is often handled by a HAM that must be familiar with the different hardware used by the organization and must interface with other management disciplines. Hardware asset management is a subset discipline of IT asset management, which deals specifically with the hardware portion of IT assets.
2.1.1 Park assets: Park asset is the assets defined as if any procurement is initiated by the organisation. Against that procurement the delivery trucks or vehicles come at the late night. So, its responsibility of one of the administrator people to wait and collect the procurement. so, we create a concept of park asset that the security person scans the QR code on the PO order through mobile app and submit so the procured asset adds into the system as a park asset. In next day the administration people come and check the park asset inventory and unboxing the delivered package and transfer that asset into the inventory.
2.1.2 Inventory: Inventory all your IT and non-IT assets, including your software licenses, with the native IT asset management capabilities of Helpdesk. Maximize the visibility of your hardware and software assets with multiple discovery modes like Windows domain scan, script scan, agent-based scan, and barcode scanning. Effectively inventory all your hardware and software assets by defining custom product types, products, and product groups. Also, keep track of the key asset financials including their depreciation information. Generate custom reports on your IT asset inventory for effective planning and budgeting. Simply we can say that inventory is a global view of all assets onboarded into the system and every action taken against the asset is through the inventory, actions like- transfer asset, assign asset, revoke asset, etc.
2.1.3 Assigned assets: Asset assignment is the process of allocating or transferring the ownership, responsibility, or usage rights of a specific asset from one individual, department, or entity to another. This practice ensures that assets are properly managed, utilized, and accounted for within an organization. Assigned asset is the tab where we map the asset to the user or employee against the employee Id. So whatever remedies or problems occur to that particular asset, then that employee has authority to raise the tickets according to problem identification through ticketing system.
2.1.4 Transferred assets: In IT Asset Management (ITAM), "transferred assets" refers to assets that have been moved from one location, department, or owner to another within an organization. This transfer may occur due to various reasons such as departmental reorganization, employee role changes, or inventory optimization. Asset Details: Essential information such as the asset ID, type (e.g., laptop, server, software license), serial number, and specifications. This data helps identify the asset uniquely. Transfer Information: The current or previous location/department/owner of the asset. The new location/department/owner where the asset is being transferred. The date on which the asset transfer takes place.
- Reason for Transfer: Justification for the asset transfer, such as role reassignment, location change, or operational need.
- Asset Status Update: Change in the status of the asset, such as “Transferred,” “In Transit” depending on its condition or transfer process.
- Ownership and Responsibility: Documentation of any changes in asset ownership or responsible personnel, along with approvals and acknowledgments.
- Inventory System Update: The IT asset management system must reflect the transfer, logging all relevant changes for traceability and compliance.
2.1.5 Others: The Others tab is provided to manage assets whose locations are not yet assigned. These assets are listed under the others tab until their location information is updated. Once the location is updated, the assets are automatically moved to the Inventory tab, where they are properly listed and managed as part of the inventory. This system ensures that assets without assigned locations are still tracked, while those with updated information are seamlessly integrated into the inventory management process.
2.1.6 Barcode Generation & QR Code: Use this method when you are using the Service tag/Serial number as the barcode value. Select the Mapping Field and choose value such as service tag, asset tag, service number etc. The selected Mapping Field value will be saved as the barcode for that asset. Once the asset is mapped with user or employee against employee id then the user itself generates the barcode according to customizable field provided and just place it on the assets for physical verification. Also, Admin and Super Admin has the authority to generate barcode for the employees. Purpose: Barcodes provide a unique identifier for each asset, allowing quick and precise asset tracking across locations and departments. Asset Labelling: A barcode is generated for each new asset and printed on a label that is affixed to the asset, which ensures easy tracking and identification.
- Instant Access to Asset Information: Scanning a QR code on an asset provides access to asset records, usage history, and maintenance logs, improving asset management without needing to retrieve data manually.
- Self-Service Support: QR codes can link to user guides, troubleshooting steps, or support contacts, empowering employees to resolve minor issues without assistance from IT.
- Maintenance Scheduling and Record-Keeping: Technicians can scan a QR code to log maintenance actions, ensuring accurate and timely record-keeping directly in the asset management system.
- Integration with Mobile Apps: QR code scanning functionality integrated with the ITAM system’s mobile app enables real-time asset updates from anywhere, enhancing asset visibility and reducing time for data entry.
Benefits in IT Asset Management
- Efficiency and Accuracy: Automated scanning reduces the need for manual entry, which speeds up workflows and minimizes errors.
- Enhanced Visibility: Barcodes and QR codes ensure easy and reliable tracking of assets throughout their lifecycle, from acquisition to disposal.
- Cost Savings: Streamlining asset tracking and maintenance activities lowers operational costs by reducing asset downtime and improving inventory control.
- Compliance and Auditing: Digital tracking through barcodes and QR codes simplifies audit preparation and helps ensure compliance with IT asset management policies.
2.2 SAM: Software Asset Management (SAM) is a critical tool designed to efficiently track, manage, and optimize software and operating system (OS) assets across an organization. It provides visibility into the software installed and operating systems running on end-user machines, such as laptops and desktops, ensuring better compliance, utilization, and management of IT resources.
The SAM module contains two primary tabs:
2.1 Software Listing: This tab displays a comprehensive list of all software installed on end-user machines. Once the client application is deployed on the devices, it scans and identifies installed applications, providing detailed insights such as software name, version, installation date, and usage statistics. This helps organizations track software licenses, detect unauthorized installations, and ensure compliance with licensing agreements.
2.2 OS Listing: This tab lists the operating systems running on the machines. It captures critical details, including the OS name, version, build, and architecture (32-bit/64-bit), providing a clear overview of the organization's OS landscape. This feature helps in monitoring OS compatibility, planning upgrades, and identifying outdated systems that may require attention.
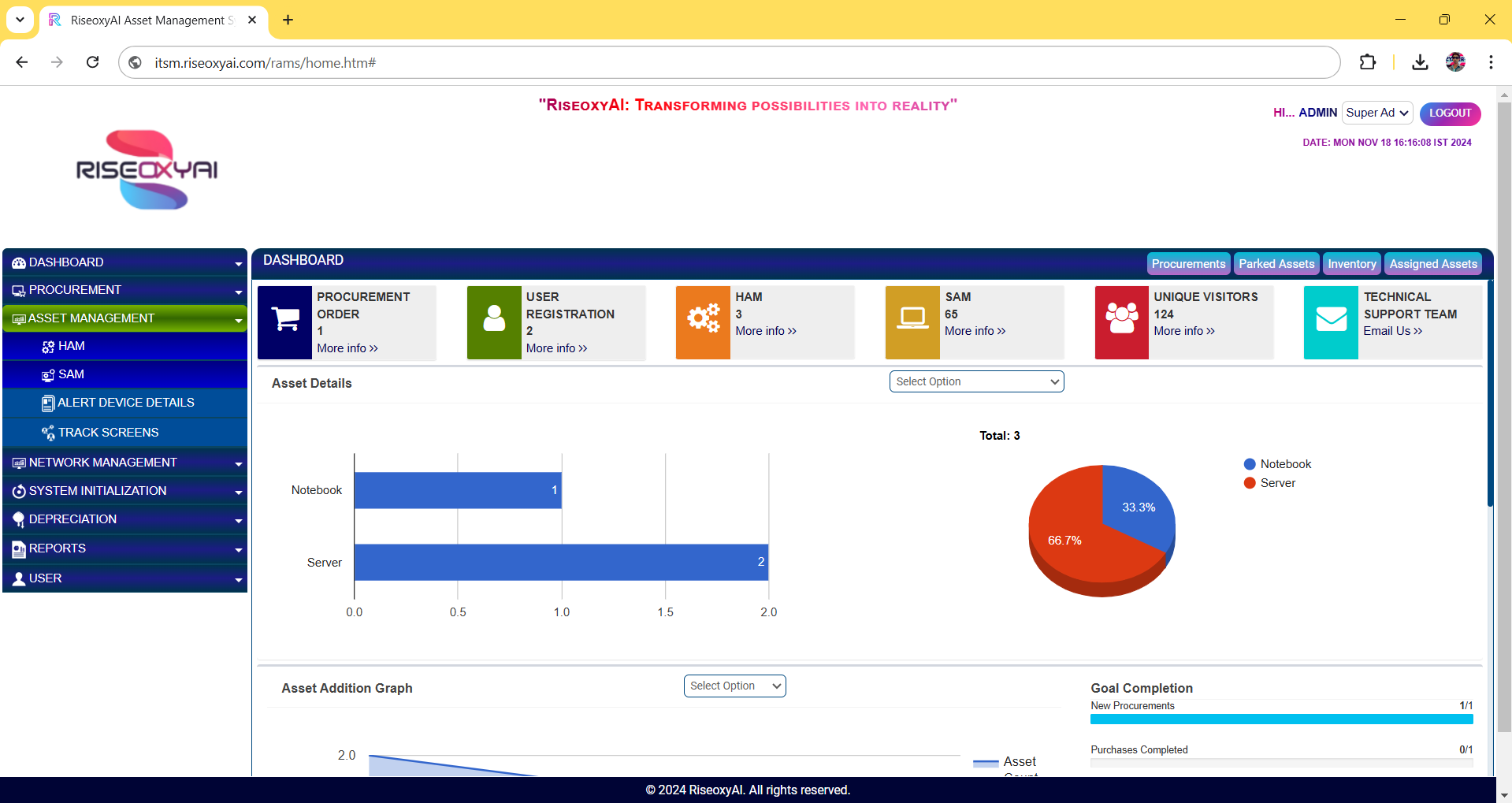
By leveraging the SAM tool, organizations can maintain a centralized inventory of software and OS assets, streamline asset tracking processes, improve license management, and enhance security by detecting and addressing non-compliant or outdated installations.
3. Data Tracking and Monitoring
3.1. Alert Device Details: An alert for device details in IT Asset Management refers to notifications triggered when specific events or conditions are met regarding a device. These alerts help IT teams proactively manage assets, maintain compliance, and prevent issues before they impact users. This feature is designed to enhance data security and prevent unauthorized data transfers by monitoring and controlling data copying activities between a laptop and an external storage device, like a USB flash drive (pen drive, external hard-disk.
- Feature Description: Data Copying Alert with Ticket Generation and Data Deletion.
- Data Copy Monitoring: When a user attempts to copy files from a laptop to a pendrive, the system automatically detects and logs this action in real-time. The monitoring system captures essential details, including the file name, size, and type, along with information about the pendrive, such as its serial number, manufacturer, storage capacity, and unique device ID.
- Automatic Alert and Ticket Generation: Upon detection of the copying attempt, an alert is triggered and an IT helpdesk ticket is generated automatically.
This ticket includes detailed information:
- User Information: Name, ID, and device details of the person attempting the transfer (emp ID). File Details: Names of files attempted to be copied, file size, and type. Pen drive Information: Device ID, serial number, and other identifiable details of the pen drive. Timestamp: Date and time of the attempted transfer. Location (if available): Physical or network location of the laptop to provide context for the security team.
- Automatic Data Removal on Pen drive: As an additional security measure, the system automatically deletes the copied file data from the pendrive, leaving only an empty file or file name visible on the device. This prevents any actual data transfer while still logging the attempted activity, deterring unauthorized data movement without fully blocking user activities. This feature ensures that no sensitive or restricted data is leaked or stored externally, supporting data privacy and security compliance.
- User Notification and Deterrence: Optionally, the user may receive a notification explaining that the copying attempt was blocked and logged, providing transparency, and serving as a deterrent for future attempts. This notification may be customized to include a reminder of the organization’s data security policies and the potential consequences of unauthorized data transfers.
- Integration with IT Security and Compliance Systems: The alert system can be integrated with broader IT security and compliance frameworks to monitor patterns of data transfer attempts, helping to identify users or devices with repeated attempts. Security teams can use this information for audits, security training, or further investigation if necessary.
Benefits of This Feature:
- Enhanced Data Security: Prevents unauthorized data transfers and protects sensitive information from being copied to external devices.
- Compliance and Audit Readiness: Ensures adherence to data protection regulations, such as GDPR, HIPAA, or internal compliance standards, by tracking and controlling data movement.
- Risk Mitigation: Reduces the risk of data breaches, insider threats, and data leakage by strictly monitoring data access and copying activities.
- Efficient Incident Response: Automated ticket generation and detailed logging enable the IT and security teams to respond quickly to potential security incidents.
- User Awareness: The deterrent effect of this feature helps to educate and remind employees of data security policies, reinforcing responsible data handling.
3.2. Track Screen: The Track Screen feature is an advanced functionality within the system that captures periodic screenshots of a user's screen at configurable intervals. This feature creates a depository of screen captures, enabling ongoing monitoring, tracking, and reference of user activity during specific tasks or interactions with the system. The Track Screen feature is particularly useful for ensuring compliance, improving security, enhancing user support, and maintaining a transparent record of user actions during critical processes.
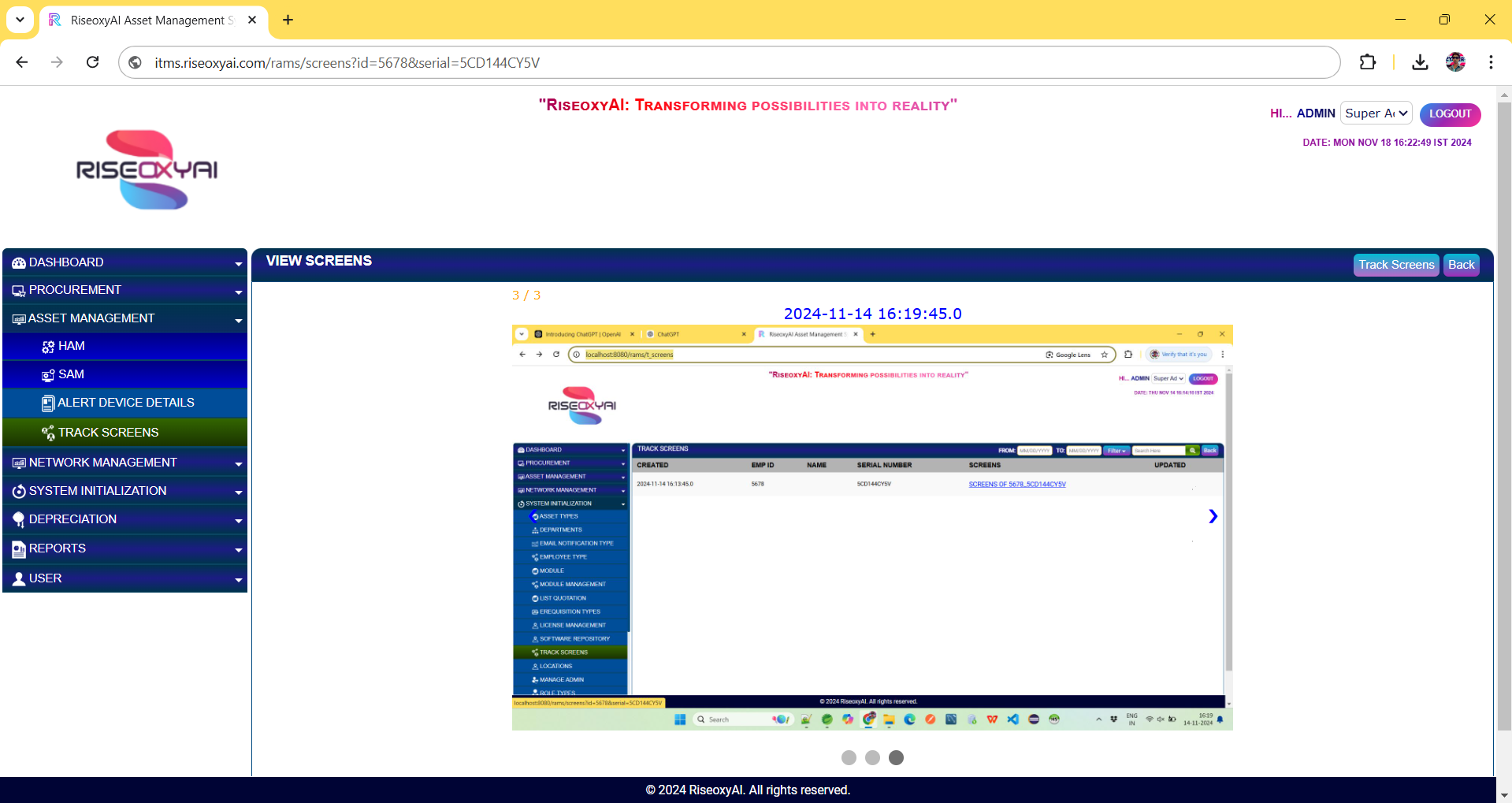
Key Features and Benefits:
- Periodic Screen Capture: The system automatically captures screenshots at configurable intervals (e.g., every minute, 5 minutes, or based on specific user actions or triggers). These screenshots are stored in a secure depository, where they can be reviewed or referenced at any time, providing a visual log of the user's screen activity.
- Configurable Intervals and Triggers: Administrators can set up customizable intervals for capturing screenshots. For example, screenshots can be taken at fixed time intervals or triggered by specific actions, such as a user opening a particular application, executing a critical task, or encountering an error. This level of configurability ensures that the tracking aligns with the organization’s monitoring needs, whether for performance, security, or troubleshooting.
- Secure and Centralized Repository: All captured screenshots are stored in a centralized, secure repository that is easily accessible for authorized personnel. The repository is designed to ensure data privacy and security, with encrypted storage and access controls to protect sensitive user data.
- User Activity Monitoring and Auditing: The feature provides a comprehensive audit trail of user activity, helping to monitor user actions during sensitive processes, such as troubleshooting or system testing. This can be particularly helpful in identifying inefficiencies, errors, or potential security risks by allowing managers or administrators to visually track how users interact with the system over time.
- Performance and Troubleshooting Support: The Track Screen feature is highly beneficial for support teams and system administrators, allowing them to review the user's screen in real-time or after the fact. This helps with troubleshooting issues that may not be easily described or reproducible by the user, offering valuable context in resolving technical problems quickly.
- Security and Compliance: For organizations that need to ensure compliance with industry regulations (e.g., financial services, healthcare), the Track Screen feature helps demonstrate adherence to security and operational standards. It can also be used to monitor for unauthorized activity or potential security breaches, as it provides a clear visual record of user actions.
- Real-Time Monitoring (Optional): Some versions of the feature may allow for real-time monitoring of user screens, providing immediate visibility of user actions without requiring retrospective access to the captured screenshots. This can be useful for high-priority incidents, where immediate intervention may be necessary to resolve a user’s issue or address a security concern.
4. Network Management
A network management is the set of applications that manage a network's independent components inside a bigger network management framework and performs several key functions. it identifies, configures, monitors, updates, and troubleshoots network devices. There are many features available in network management like SNMP scan, managing SNMP devices, monitoring network devices, etc. Network monitoring, also frequently called network management, is the practice of consistently overseeing a computer network for any failures or deficiencies to ensure continued network performance. Technically, network monitoring can be viewed as a subset of network management, but the two are considered equivalent in practice. In this another feature is link management that manages the network related links region wise and shows the Active and Inactive links in link dashboard. Inactive links shows with red colour and blink continuously and upon over shows the details of link.
The Network Monitoring module offers a suite of tools for real-time tracking and management of network performance across an organization’s IT infrastructure. Key sub-modules include SNMP Scan, which automatically detects and categorizes SNMP-enabled devices such as routers, switches, and firewalls; the SNMP Device Dashboard, which provides a comprehensive view of network elements and their utilization metrics; and Link Management, featuring a dashboard that measures and reports on network link performance, with color-coded indicators and audible alarms for issues like link downtime. Additionally, the Bandwidth Management and Monitoring sub-module tracks bandwidth usage across various geographic locations, offering audio-visual alerts for issues such as high traffic, low consumption, or link outages. These sub-modules work together to provide intuitive, real-time insights into network health, ensuring quick identification and resolution of potential issues, and helping maintain optimal network performance across the organization.
The RAMS server is a self-healing system that monitors and analyses RAM, CPU, and HDD utilization, displaying usage trends through date-filtered graphs on its dashboard. It includes features to start or stop the self-healing mechanism, highlights maximum-utilized parameters in red, generates alerts, and sends notification emails to the Super Admin. Additionally, it performs heartbeat monitoring of servers, tracking parameters like uptime and downtime.
5. System Initialization
The System Initialization module is the core configuration engine of the system, acting as the foundation for system setup and data initialization. It serves as the central interface through which administrators configure the system, preparing it for full deployment and use across the organization. By enabling the configuration of essential parameters and core data, the System Initialization module ensures that the system operates efficiently, aligns with organizational requirements, and supports business processes from day one.
The System Initialization module is integral to the system’s operational readiness. It provides administrators with the tools to customize and configure system settings, user roles, asset management, procurement processes, and more. Here are some of the key functionalities within this module:
Key Features of the System Initialization Module:
- Asset Management Configuration: Add/Remove Asset Type, Administrators can define and manage various asset categories (e.g., hardware, software, office equipment, etc.), ensuring that the system tracks and organizes assets according to the organization’s structure. This functionality allows for easy addition or deletion of asset types, enabling the system to remain flexible and adaptable to changing asset management requirements.
- Department and Organizational Structure Setup: Add/Delete Departments, the module enables the configuration of the organization’s internal structure by adding or removing departments. This ensures that all workflows, permissions, and reporting structures are aligned with the organization’s hierarchy. Administrators can also assign employees to specific departments, roles, and functions within the system.
- Role and Permission Management: Role-Based Access Control (RBAC), The module serves as the backbone for user role management. Administrators can define different employee types (e.g., admin, manager, technician, etc.), assign roles to users, and determine access permissions based on these roles. This ensures that each user has the appropriate level of access to the system’s features, data, and resources based on their job responsibilities, enhancing security and operational efficiency.
- Email Notifications and Alerts: The module facilitates the setup of email notifications for various system events, including ticket updates, escalations, asset status changes, approval workflows, and more. Notifications can be customized to ensure users and stakeholders are informed in a timely manner about critical system activities or changes.
- Vendor Registration and Quotation Management: The System Initialization module supports the management of vendor relationships by allowing administrators to configure and maintain a list of registered vendors. Quotation Management: Administrators can configure the system to handle quotations from vendors, ensuring that procurement activities are properly managed and tracked. The module ensures that vendor information is up to date, allowing for efficient vendor selection and evaluation in the procurement process.
- Procurement Configuration: Administrators can define different types of procurement requisitions (e.g., planned, ad-hoc, urgent) to streamline the procurement process. The system can be configured to automatically route requisitions to appropriate departments or approvers based on predefined criteria, helping to maintain procurement efficiency and compliance.
- License and Subscription Management: The module provides tools for managing software and hardware licenses. Administrators can define license types, expiration dates, and usage limits. This feature helps organizations track and manage software compliance, preventing overuse or underuse of licensed resources.
- System Alerts and Monitoring: The module allows administrators to configure system alerts that notify users or administrators about important system events, such as failed processes, security breaches, or performance issues. These alerts help maintain system health and ensure that issues are quickly addressed, minimizing downtime, and maximizing productivity.
- Data Import/Export: To facilitate system migration or initial setup, the System Initialization module supports bulk data import/export functionality. This allows administrators to quickly load essential data (e.g., employee records, asset details, vendor information) into the system from external files or databases.
- User and Workflow Customization: The module provides the flexibility to define custom workflows for different processes, such as approvals, ticket escalations, and procurement approvals. Workflows can be customized based on user roles, departments, or asset categories, enabling streamlined, automated operations.
6. Reports
The system provides 16 default, comprehensive reports at deployment, created through mutual agreement, which are automatically generated and shared via email and the dashboard for insightful analysis. The Reports Module in the system is a powerful feature designed to provide insightful analytics and data visualization for effective decision-making. It offers a wide range of pre-configured and customizable reports, ensuring comprehensive coverage of system activities and performance metrics. Users can generate reports based on various parameters, including date ranges, user activities, and resource utilization.
Key features of this module include:
- Default Reports: At deployment, the system provides 16 pre-configured reports, tailored to meet organizational needs through mutual agreement.
- Customizable Reports: Users can define specific criteria and filters to generate reports that cater to unique business requirements.
- Automated Report Generation: Reports are automatically created and pushed to the dashboard and email, ensuring timely availability without manual intervention.
- Visual Insights: Graphs and charts in reports provide a clear and holistic view of parameters like RAM, CPU, HDD utilization, uptime/downtime, and user interactions.
- Alerts and Notifications: The module integrates with the system’s alert mechanism, highlighting critical insights, such as over-utilization, directly within the reports.
- Export and Sharing: Reports can be downloaded in various formats (PDF, Excel) and shared with stakeholders for collaboration and record-keeping.
7. User Configuration
The system includes a comprehensive module with several sub-modules to enhance user account management and system interaction. Change Password Console allows users to update their passwords securely, while the Reset Password Console facilitates password recovery in case of loss. The User History Tab provides a detailed log of all user interactions with the platform, serving as a historical archive, even for users who have been deleted from the system. The User List displays all active and inactive users, enabling administrators to manage user accounts efficiently. Additionally, the View Profile Tab allows users to view and update their profiles, including personal details, contact information, and preferences, ensuring data accuracy. The system also supports Bulk User Upload, enabling administrators to register and activate multiple users at once using Excel sheets, streamlining onboarding processes for large teams or organizations. This module strengthens system usability, enhances user data management, and provides critical insights for activity tracking and operational efficiency.
For a demo, please reach out to us at: info@riseoxyai.com
If you have any questions or need support, feel free to contact us at: support@riseoxyai.com